Protecting the Internet
| Author: | Lloyd Kvam, Venix Corp |
|---|---|
| Date: | 2007-02-13 |
Outline
motivation
needed to isolate a compromised Windows web server while allowing it to continue to function as a web server.
that is, filter out the bad packets while allowing the good packets
do this without changing the network configuration or the router
iptables
- what it does (state-full packet inspection)
- how it is configured
- how this provides a firewall (accept, reject, drop)
- explicitly configured in network - (visible)
- operates in a specific host or in a router
bridging
- connecting networks at the LAN (ethernet) level
- ethernet switches are bridges
- forwards ethernet frames between segments
ebtables
- what it does (inspects ethernet frames)
- also understands ip information in frames
- how it is configured
- also provides accept, drop
- implicitly configured in network - (invisible)
- copies frames between network segments
openwrt
- linux for routers
- installing and configuring
- (rules of engagement - not like normal linux configuration)
linksys wrt54gl
specifics of openwrt for inexpensive linux device
Presenter
Lloyd Kvam
President, Venix Corp
Venix provides technical services
- Software Development
- System Administration
- Network Planning, Administration and Configuration
- Security Assistance
Motivation
ISP notified friends who have a Windows server that it had been compromised. The server was directly attached to the Internet router provided by the ISP. Subsequent investigation showed they had been hit by a zero-day worm. The signature update was not released until almost a week after they had been hit.
The ISP was not prepared to block ports on the local router. My friends were desperate to keep their server on-line. They had no alternative computer ready to deploy . They did have a Linksys WRT54GL purchased for home use.
I volunteered to configure the WRT54GL to block all malicious traffic.
How hard could it be?
IPTables Background
http://iptables-tutorial.frozentux.net/iptables-tutorial.html
Provides state-full packet inspection
Configured to accept, reject, drop packets
Organized into Tables based on packet processing stage
raw mangle nat filter
Chains of rules in each table
Firewall uses filter table and INPUT nad FORWARD chains
Configuring iptables
iptables --list --verbose
My laptop iptables
iptables --list --verbose:
Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 4736K 298M RH-Firewall-1-INPUT all -- any any anywhere anywhere - Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 RH-Firewall-1-INPUT all -- any any anywhere anywhere - Chain OUTPUT (policy ACCEPT 9371K packets, 14G bytes) pkts bytes target prot opt in out source destination - Chain RH-Firewall-1-INPUT (2 references) pkts bytes target prot opt in out source destination 44603 12M ACCEPT all -- lo any anywhere anywhere 4685K 282M ACCEPT all -- any any 192.168.0.0/24 anywhere 7 728 ACCEPT icmp -- any any anywhere anywhere icmp any 0 0 ACCEPT esp -- any any anywhere anywhere 0 0 ACCEPT ah -- any any anywhere anywhere 52 20225 ACCEPT udp -- any any anywhere 224.0.0.251 udp dpt:mdns 0 0 ACCEPT udp -- any any anywhere anywhere udp dpt:ipp 0 0 ACCEPT udp -- any any anywhere anywhere udp dpt:tftp 6158 4847K ACCEPT all -- any any anywhere anywhere state RELATED,ESTABLISHED 0 0 ACCEPT tcp -- any any anywhere anywhere state NEW tcp dpt:ssh 0 0 ACCEPT tcp -- any any anywhere anywhere state NEW tcp dpt:http 0 0 ACCEPT tcp -- any any anywhere anywhere tcp dpts:6881:iatp-normalpri flags:SYN,RST,ACK/SYN 95 24690 REJECT all -- any any anywhere anywhere reject-with icmp-host-prohibited
iptables [-t table] -[AD] chain rule-specification [options]
-A is append rule -D is delete rule (either the matching rule or by number (1,2,...) -P is policy when no rule matches filter is the default table chains INPUT, FORWARD, OUTPUT firewall rules usually go in the INPUT and FORWARD chains Do this by specifying firewall chain as target in bot
iptables-save
writes current rules to stdout
/etc/sysconfig/iptables
default source of rules in fedora core 6 distribution I edit file to add comments and save changes service iptables restart
Using IP Tables
- operates in router or host
- host and router are visible on network
must be configured into the network. You can not simply add an additional router to a network without changing configurations
Bridging Background
- connects networks at the LAN (ethernet) level
- ethernet switches are bridges
- copies frames between ports
- bridge is invisible to TCP/IP
- smart -- only copies to destination port
- addressing based on MAC address
- ports can be grouped as a unit (VLAN)
Wrt54gl diagram
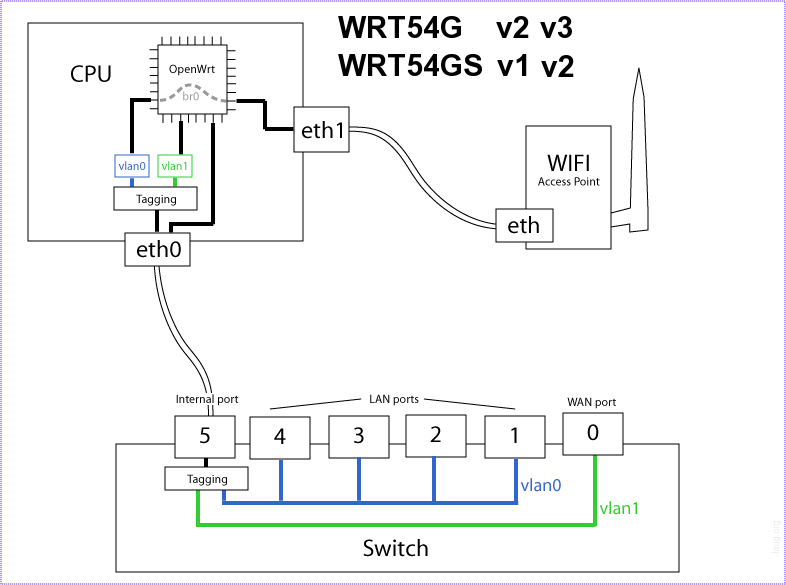
Sample Bridge (from wrt54gl)
root@OpenWrt:/etc# brctl show:
bridge name bridge id STP enabled interfaces
br0 8000.001217122699 yes vlan0
eth1
EB Tables Background
http://freshmeat.net/articles/view/1433/
- provides tables and chains of rules for processing LAN frames
- borrows nomenclature from iptables
- understands ip header information
ebtables summary
- inspects ethernet frames
- also understands tcp/ip information in frames
- also provides accept, drop
- implicitly configured in network - (invisible)
- copies frames between network segments
Protection Strategy
- Use ebtables to avoid network config changes
- Break vlan0 into two vlans with ebtables to filter frames
- Save this on the WRT54GL so that it would reboot in filtering mode
My protective ebtables config
ebtables --list Bridge table: filter Bridge chain: INPUT, entries: 0, policy: ACCEPT Bridge chain: FORWARD, entries: 23, policy: ACCEPT -p ARP -j ACCEPT -p IPv4 -s 0:aa:aa:aa:aa:aa -i vlan2 --ip-proto tcp --ip-dport 80 -j ACCEPT -p IPv4 -s 0:aa:aa:aa:aa:aa -i vlan2 --ip-proto udp --ip-dport 53 -j ACCEPT -p IPv4 -s 0:bb:bb:bb:bb:bb -i vlan2 --ip-proto tcp --ip-dport 80 -j ACCEPT -p IPv4 -s 0:bb:bb:bb:bb:bb -i vlan2 --ip-proto udp --ip-dport 53 -j ACCEPT # -p IPv4 -d 0:aa:aa:aa:aa:aa -i vlan0 --ip-proto tcp --ip-sport 80 -j ACCEPT -p IPv4 -d 0:aa:aa:aa:aa:aa -i vlan0 --ip-proto udp --ip-sport 53 -j ACCEPT -p IPv4 -d 0:bb:bb:bb:bb:bb -i vlan0 --ip-proto tcp --ip-sport 80 -j ACCEPT -p IPv4 -d 0:bb:bb:bb:bb:bb -i vlan0 --ip-proto udp --ip-sport 53 -j ACCEPT -s 0:aa:aa:aa:aa:aa -i vlan2 -j DROP -s 0:bb:bb:bb:bb:bb -i vlan2 -j DROP -d 0:bb:bb:bb:bb:bb -i vlan0 -j DROP -d 0:aa:aa:aa:aa:aa -i vlan0 -j DROP Bridge chain: OUTPUT, entries: 0, policy: ACCEPT
openwrt
- basic web interface
- package management (ipkg)
- squashfs preserves originals (training wheels)
wrt54GL notes
- (Original LAN address is 192.168.1.1)
- (my demo router is at 192.168.0.55)
- (default credentials: admin, admin)
- flashed openwrt (white russian) squashfs
- installed ebtables
wrt54GL features
- used ipkg to install ebtables. ebtables kernel modules not loaded automatically. I had to update boot scripts
- configure many aspects through nvram variables
- nvram command help omits commit
- nvram commit saves changes for future reboots
- standard system files are symbolic links to squashfs in /rom
configuring openwrt
- web interface supports general configuration parameters
- commandline interface needed for flexibility
- use of nvram variables simplifies configuration changes
- great platform for ad hoc network appliance
What I did to block all other traffic
This is not guaranteed complete, but should be close:
nvram set vlan2ports="3 4 5" nvram set vlan0ports="1 2 5*" nvram set vlan2hwname=et0 # # vlan0 was started by ifup lan # so I created an interface named man # (simply stepping down alphabet) nvram set man_ifname=vlan2 nvram set man_proto=static # added man to /etc/init.d/S40network ifup wan + ifup man ifup wifi # the ebtables modules were not loaded (insmod) by default # # added them to /etc/modules.d/40-ipt-nat-extra # (Perhaps I should have created a nerw file) # cat 40-ipt-nat-extra ebtables ebt_802_3 ebt_among ebt_arp ebt_arpreply ebt_dnat ebt_ip ebt_limit ebt_log ebt_mark ebt_mark_m ebt_pkttype ebt_redirect ebt_snat ebt_stp ebt_ulog ebt_vlan ebtable_broute ebtable_filter ebtable_nat ip_conntrack_amanda ip_conntrack_proto_gre ip_nat_proto_gre ip_conntrack_pptp ip_nat_pptp ip_nat_snmp_basic ip_conntrack_tftp ip_nat_tftp ip_conntrack_h323 ip_nat_h323 ip_conntrack_rtsp ip_nat_rtsp added ebtables filter rules (shown above) to /etc/firewall.user # DO NOT FORGET nvram commit
basic network configuration NVRAM variables:
NVRAM Description
<name>_ifname The name of the linux interface the settings apply to
<name>_ifnames Devices to be added to the bridge (only if the above is a bridge)
<name>_proto The protocol which will be used to configure an IP
static: Manual configuration (see below)
dhcp: Perform a DHCP request
pppoe: Create a ppp tunnel
<name>_ipaddr ip address (x.x.x.x)
<name>_netmask netmask (x.x.x.x)
<name>_gateway Default Gateway (x.x.x.x)
<name>_dns DNS server (x.x.x.x)
<name>_hostname hostname requested with dhcp
<name>_hwaddr MAC address (aa:bb:cc:dd:ee:ff)
if you want to use a different MAC from the ROM
The command ifup <name> will configure the interface defined by
<name>_ifname according to the above variables.
The only <name> with any significance is wan, used by the
/etc/init.d/S45firewall script. The firewall script will NAT traffic
through the wan_ifname, blocking connections to wan_ifname.